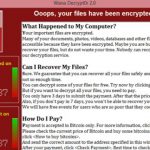
 On Friday May 12th, “WannaCry” ransomware made its first appearance in Europe. Within 72 hours, it had spread to 150 countries. Ransomware is software that locks you out of the files on your computer. It will ask you to send money (usually in bitcoin currency) in order to unlock your files. Paying the ransom is not recommended as it does not guarantee the attackers will unlock your files and it funds future cyberattacks.
On Friday May 12th, “WannaCry” ransomware made its first appearance in Europe. Within 72 hours, it had spread to 150 countries. Ransomware is software that locks you out of the files on your computer. It will ask you to send money (usually in bitcoin currency) in order to unlock your files. Paying the ransom is not recommended as it does not guarantee the attackers will unlock your files and it funds future cyberattacks.
This particular ransomware affects Windows 8.1, Windows 7, Windows Vista and Windows Server (2008, 2008 R2, 2012, 2012 R2, 2016). In March, Microsoft released an update that protects computers against the method of attack that this ransomware uses. This means if you regularly apply Windows Updates, the ransomware will not affect you. If you’re using an out-of-support version of Windows, like Windows 8, Windows XP or Windows Server 2003, Microsoft has released updates here.
Over the weekend a security researcher inadvertently activated a kill switch for WannaCry, significantly slowing its spread. There are multiple variants of WannaCry that do not have a kill switch and continue to spread; there is also a risk of “copycat” attacks being developed that would spread using the same method of attack.
Takeaways:
- Regularly apply updates to your computer
- Always have backups in place
- Don’t open up email attachments from people you don’t know
To read more about how this ransomware came to be, and how others like it are on the way see this article:
The next ransomware attack will be worse than WannaCry

nice article !! thanks for providing this information and making us aware of WannaCry Ransomware Attack !!
very informative article many too many pcs very after by this attack