Using Tabletop Exercises to Improve SMB Cybersecurity
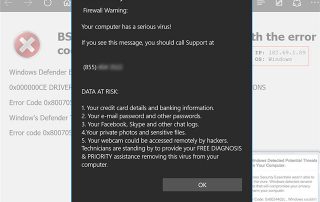
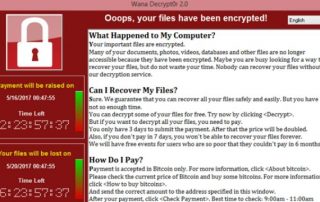
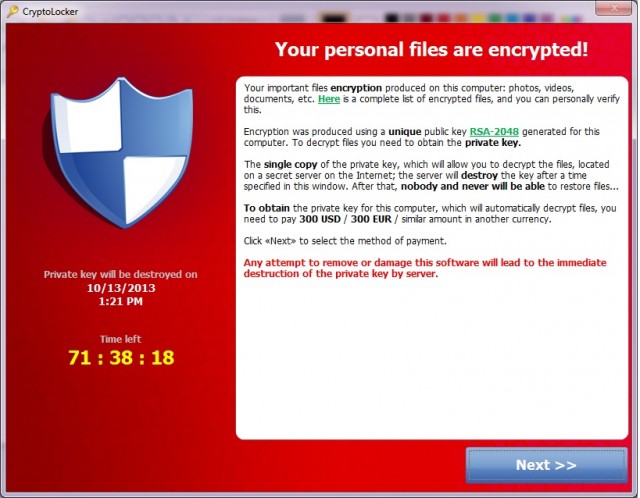
YOU HAVE a jillion things to do to keep your organization humming. What's the best use of your time and budget when it comes to cybersecurity? If you already have some network cybersecurity systems in place, tabletop exercises are a great way to go. They'll help establish or improve policies, playbooks, and staff training -- [...]